Vulnerability Scanning Tools Market Size (2024 – 2030)
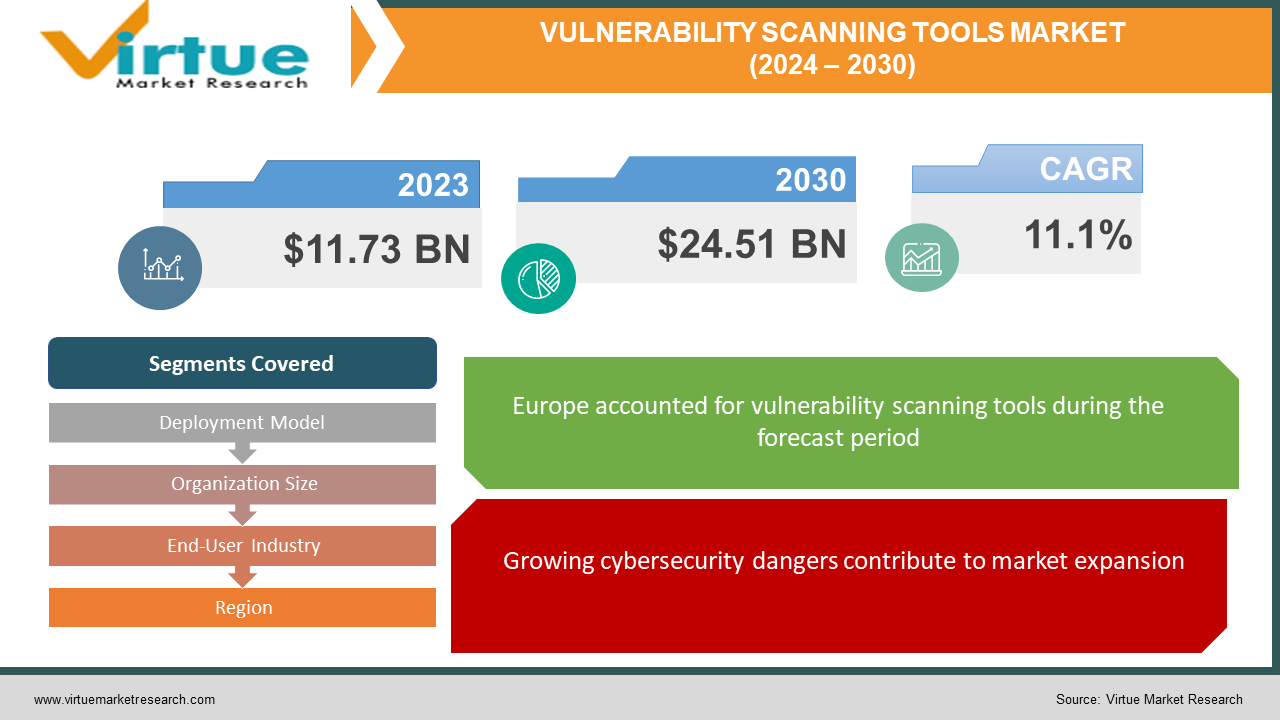
The global Vulnerability Scanning Tools Market size was exhibited at USD 11.73 billion in 2023 and is projected to hit around USD 24.51 billion by 2030, growing at a CAGR of 11.1% during the forecast period from 2024 to 2030.
Vulnerability scanning technologies are like automatic scouts in the battle for digital security; they are always looking for holes in your systems. These software programs painstakingly go over computers, networks, and programmes, looking for weaknesses such as obsolete software, incorrect settings, weak passwords, missing security patches, and unneeded services. By utilising an extensive database of known vulnerabilities, this thorough scan can identify possible security breaches before hackers take advantage of them. There are many advantages to using these digital defences. Organisations can greatly enhance their overall security posture by prioritising patching and remedial efforts based on the identification of these issues. By being proactive, you can lessen the likelihood of assaults because attackers will find it harder to target vulnerabilities. Furthermore, vulnerability scanning technologies make it easier to comply with requirements that require strong security measures by offering insightful information about potential security holes. The best tool for you will rely on your unique requirements. Like electronic spies, network vulnerability scanners search for vulnerabilities in all your network's systems and devices. Conversely, web application scanners employ a more focused strategy, functioning as virtual microscopes to pinpoint vulnerabilities within individual online apps. The size of the network, cost, and user-friendliness are all important factors to consider when choosing the best scanning tool for your company. Industry mainstays with a variety of features and functions, such as Nessus, OpenVAS, Tenable, Qualys VM, and Acunetix, are also popular choices.
Key Market Insights:
The market for vulnerability scanning technologies has grown significantly in recent years, and it is anticipated that this trend will continue in the years to come. The use of vulnerability scanning tools to identify and reduce security threats has increased due to the rise in cyberattacks and data breaches in a variety of industries. The market for vulnerability scanning tools has expanded due in part to the growing number of connected devices and the growing use of cloud-based services. Growth in the market is also anticipated to be fuelled by the adoption of laws and compliance guidelines by the government to protect data security and privacy. Because of the existence of significant industry participants, the early adoption of cutting-edge technologies, and the rise in cyberattacks, North America is anticipated to hold the biggest market share in the vulnerability scanning tools market. Due to the rising number of internet users and the uptake of cloud-based services in developing nations like China and India, the Asia-Pacific region is also expected to experience considerable growth throughout the projection period.
Global Vulnerability Scanning Tools Market Drivers:
Growing cybersecurity dangers contribute to market expansion:
Organisations are becoming acutely aware of the critical need to protect their digital assets in the face of an onslaught of cyberattacks and data breaches. The need for vulnerability scanning solutions has increased because of this. These solutions continuously scan the network and systems of an organisation for vulnerabilities, acting as digital security guards. Vulnerability scanning is a multifaceted method to strengthen an organization's security posture by proactively detecting and correcting these vulnerabilities before attackers exploit them. First, it makes proactive threat detection possible, revealing security flaws before an intrusion may occur. This considerably lowers the possibility of data breaches, which can have disastrous effects on one's finances and reputation. Additionally, by giving a clear picture of an organization's security posture and emphasising areas for improvement, vulnerability scanning assists organisations in adhering to data privacy rules. These scanners also rank vulnerabilities according to severity, which enables security teams to concentrate their efforts on the most important problems. Finally, enhanced vulnerability scanning provides ongoing observation, guaranteeing that a company's defences remain current against ever-changing cyberthreats. Vulnerability scanning tools have essentially become a vital tool for enterprises to strengthen their defences and negotiate the ever-more-dangerous digital terrain.
Tight data privacy laws contribute to the market's expansion.
Governments everywhere are imposing more stringent laws like the CCPA and GDPR as concerns about data privacy grow. Organisations who violate these laws risk incurring significant fines for failing to protect user data. Businesses are increasingly using vulnerability detection solutions to help them traverse this new terrain. These technologies serve as compliance companions, spotting security flaws within an organisation that may result in data breaches and subsequent penalties. Vulnerability scans help organisations prioritise remedial efforts and make sure they comply with data protection standards by highlighting these issues. Additionally, in the event of a data breach inquiry, regular vulnerability scans with fixed vulnerabilities provide documented evidence of an organization's due diligence. Furthermore, the ability to continuously monitor an organization's security posture by changing rules is provided by sophisticated scanners. Essentially, vulnerability scanning gives companies the chance to show their dedication to data safety while simultaneously protecting sensitive information, which might help them avoid large fines and build consumer trust.
Global Vulnerability Scanning Tools Market Restraints and Challenges:
There are many obstacles and limitations facing the worldwide market for vulnerability scanning products. These include the speed at which the threat landscape is evolving and the complexity of contemporary IT systems, which can exceed the capabilities of scanning technologies and result in potential holes in security coverage. Scan efficacy can be compromised by false positives or negatives, and resource-intensive scanning activities provide challenges to resource-constrained organisations. Adoption is made more difficult by the need to manage expenses, integrate with current systems, and comply with legal and regulatory requirements. The proper deployment and use of vulnerability scanning technologies are further complicated by the need for user education and training, the incapacity to identify zero-day vulnerabilities and the possibility of vendor lock-in.
Global Vulnerability Scanning Tools Market Opportunities:
Considering the changing cybersecurity landscape, there are substantial prospects for growth and innovation in the global market for vulnerability scanning products. There is a rising need for cutting-edge scanning solutions due to the rise in cyber threats and the growing attack surface caused by cloud computing and IoT usage. AI-powered and automated solutions are becoming more and more popular, providing enterprises with enhanced risk assessment skills, and streamlined security operations. The regulatory compliance aspect and integration with SOAR platforms provide even more value to these technologies. Additionally, vendors can increase their market reach, take advantage of new opportunities, and maintain their competitiveness in the quickly changing cybersecurity market by branching out into various industrial sectors and forming alliances with other cybersecurity vendors and industry players.
VULNERABILITY SCANNING TOOLS MARKET REPORT COVERAGE:
|
REPORT METRIC |
DETAILS |
|
Market Size Available |
2023 - 2030 |
|
Base Year |
2023 |
|
Forecast Period |
2024 - 2030 |
|
CAGR |
11.1% |
|
Segments Covered |
By Deployment Model, Organization Size, End-User Industry, and Region |
|
Various Analyses Covered |
Global, Regional & Country Level Analysis, Segment-Level Analysis, DROC, PESTLE Analysis, Porter’s Five Forces Analysis, Competitive Landscape, Analyst Overview on Investment Opportunities |
|
Regional Scope |
North America, Europe, APAC, Latin America, Middle East & Africa |
|
Key Companies Profiled |
Acunetix Ltd., BeyondTrust Corporation, F-Secure Corporation, IBM Corporation, McAfee LLC, Nessus, Qualys, Inc., Rapid7 LLC, Tenable, Inc., Tripwire, Inc. |
Global Vulnerability Scanning Tools Market Segmentation: By Deployment Model
-
On-Premises
-
Cloud-Based
One significant segmentation element for the market for vulnerability scanning technologies is the kind of deployment. While cloud-based vulnerability scanning tools are housed on a cloud server and accessed via the Internet, on-premises vulnerability scanning solutions are installed and operated within the organization's premises. One of the key industry trends is the growing use of cloud-based vulnerability scanning technologies. The adoption of cloud-based technologies is being fuelled by benefits like cost-effectiveness, scalability, and flexibility that they provide. Additionally, the need for cloud-based vulnerability assessment solutions is expected to increase due to the expansion of remote work and cloud-based infrastructure. Furthermore, the usage of vulnerability scanning technologies in the cloud is being driven by the movement towards DevSecOps, which incorporates security into the software development process. The desire for more control and customisation over the scanning tools is expected to fuel the growth of the on-premises deployment market. In general, it is anticipated that both deployment models would coexist and serve various client demands in the market for vulnerability scanning products.
Global Vulnerability Scanning Tools Market Segmentation: By Organization Size
-
Small and Medium-Sized Enterprises (SMEs)
-
Large Enterprises
Based on the size of the organisation, the vulnerability scanning tools market may be divided into two segments: major companies and small and medium-sized enterprises (SMEs). The number of cyberattacks on both small and large organisations has increased in the past several years. Consequently, there has been a shift in the emphasis on cybersecurity, with companies of all kinds investing in vulnerability assessment technologies to safeguard their systems and networks from online attacks. Due to their affordability and simplicity of use, cloud-based vulnerability screening technologies are becoming more and more popular among small and medium-sized businesses (SMEs). These companies don't have a lot of money or resources to spend on cybersecurity solutions, so cloud-based vulnerability detection technologies offer an affordable, scalable alternative. However, major businesses may afford to purchase both cloud-based and on-premises vulnerability scanning products. All company sizes are expected to see a rise in the requirement for vulnerability scanning technologies in the upcoming years due to the proliferation of cyber threats and the growing demand for strong cybersecurity defences.
Global Vulnerability Scanning Tools Market Segmentation: By End-User Industry
-
Government and defence
-
IT and telecom
-
BFSI
-
Healthcare
-
Retail
-
Others
Many companies utilise vulnerability scanning technologies extensively to find and fix security flaws in their IT infrastructure. The market can be divided into government and defence, IT and telecom, BFSI, healthcare, retail, and other end-use industries. The necessity to secure vital infrastructure and the rising frequency of cyberattacks are expected to propel the government and defence industry to a commanding market share. The expanding use of cloud-based services and the increasing acceptance of IoT devices are expected to drive significant growth in the IT and telecom sectors. Because of the necessity of safeguarding financial data and transactions, the BFSI industry is anticipated to be another significant driver of market growth. The integration of vulnerability scanning tools with other security solutions, such as threat intelligence platforms and security information and event management (SIEM), has become increasingly popular in terms of market trends. Organisations can now approach threat identification and response with greater comprehensiveness and automation thanks to this feature. Furthermore, cloud-based vulnerability scanning technologies are becoming more and more popular since they are more affordable, flexible, and scalable than on-premises alternatives.
Global Vulnerability Scanning Tools Market Segmentation: By Region
-
North America
-
Asia-Pacific
-
Europe
-
South America
-
Middle East and Africa
The Middle East & Africa, Asia Pacific, North America, Europe, and South America make up the regional segments of the vulnerability scanning tools market. Due to the presence of numerous major competitors and the high level of acceptance of cutting-edge security solutions in the area, North America is anticipated to dominate the market throughout the projected decade. Furthermore, the necessity to comply with government laws and growing concerns about cyberattacks are fuelling the expansion of this industry. Bring-your-own-device (BYOD) rules in companies and the growing acceptance of cloud-based services are expected to propel considerable growth in the Asia Pacific region over the forecast year. The requirement for security measures and the increase in cyber threats are also driving the growth of this market in this area. The market for vulnerability scanning tools is anticipated to develop significantly throughout the forecast period in all regions due to the growing significance of cybersecurity and the increasing frequency of cyberattacks that target businesses of all kinds.
COVID-19 Impact Analysis on the Global Vulnerability Scanning Tools Market:
The pandemic had a wide range of consequences on the market for vulnerability scanning technologies worldwide. On the one hand, firms now have a larger attack surface due to the increase in remote work. Securing remote devices and cloud infrastructure became critical as personnel and data got dispersed outside of typical office environments. To find and address vulnerabilities in these dispersed systems, this increased demand for vulnerability scanners. Organisations also made more investments in cybersecurity solutions, such as vulnerability scanning tools, because of increased awareness of cyberattacks during the epidemic that targeted vulnerable systems and remote workers. It brought with it difficulties as well. The adoption of vulnerability scanners may have been impacted by some firms cutting back on spending and delaying or eliminating investments in non-essential security solutions because of economic uncertainties brought on by the epidemic. Moreover, the manufacturing and distribution of hardware and software, including vulnerability assessment tools, were hampered by interruptions in international supply chains. For certain organisations, this might have resulted in deployment and upgrade delays.
Recent Trends and Developments in the Global Vulnerability Scanning Tools Market:
The network monitoring and visibility business NetFort has been acquired by the cybersecurity startup Rapid7. With this acquisition, Rapid7 hopes to strengthen its vulnerability management portfolio and increase the scope of its product offerings in the market for vulnerability scanning tools. Tenable.io Container Security has been released, according to Tenable, a top supplier of vulnerability management solutions. With more businesses incorporating containerisation into their cloud architecture, there is a growing need for vulnerability scanning tools in container settings. This new solution was developed to fulfil this need. The new Vulnerability Management, Detection, and Response (VMDR) solution from cloud-based security and compliance solutions vendor Qualys has been announced. The new solution combines threat detection, vulnerability management, and response capabilities into a single platform to give organisations a more thorough and efficient approach to vulnerability management.
Key Players:
-
Acunetix Ltd.
-
BeyondTrust Corporation
-
F-Secure Corporation
-
IBM Corporation
-
McAfee LLC
-
Nessus
-
Qualys, Inc.
-
Rapid7 LLC
-
Tenable, Inc.
-
Tripwire, Inc.
Chapter 1. Vulnerability Scanning Tools Market – Scope & Methodology
1.1 Market Segmentation
1.2 Scope, Assumptions & Limitations
1.3 Research Methodology
1.4 Primary Sources
1.5 Secondary Sources
Chapter 2. Vulnerability Scanning Tools Market – Executive Summary
2.1 Market Size & Forecast – (2024 – 2030) ($M/$Bn)
2.2 Key Trends & Insights
2.2.1 Demand Side
2.2.2 Supply Side
2.3 Attractive Investment Propositions
2.4 COVID-19 Impact Analysis
Chapter 3. Vulnerability Scanning Tools Market – Competition Scenario
3.1 Market Share Analysis & Company Benchmarking
3.2 Competitive Strategy & Development Scenario
3.3 Competitive Pricing Analysis
3.4 Supplier-Distributor Analysis
Chapter 4. Vulnerability Scanning Tools Market Entry Scenario
4.1 Regulatory Scenario
4.2 Case Studies – Key Start-ups
4.3 Customer Analysis
4.4 PESTLE Analysis
4.5 Porters Five Force Model
4.5.1 Bargaining Power of Suppliers
4.5.2 Bargaining Powers of Customers
4.5.3 Threat of New Entrants
4.5.4 Rivalry among Existing Players
4.5.5 Threat of Substitutes
Chapter 5. Vulnerability Scanning Tools Market – Landscape
5.1 Value Chain Analysis – Key Stakeholders Impact Analysis
5.2 Market Drivers
5.3 Market Restraints/Challenges
5.4 Market Opportunities
Chapter 6. Vulnerability Scanning Tools Market – By Deployment Model
6.1 Introduction/Key Findings
6.2 On-Premises
6.3 Cloud-Based
6.4 Y-O-Y Growth trend Analysis By Deployment Model
6.5 Absolute $ Opportunity Analysis By Deployment Model, 2024-2030
Chapter 7. Vulnerability Scanning Tools Market – By Organization Size
7.1 Introduction/Key Findings
7.2 Small and Medium-Sized Enterprises (SMEs)
7.3 Large Enterprises
7.4 Y-O-Y Growth trend Analysis By Organization Size
7.5 Absolute $ Opportunity Analysis By Organization Size, 2024-2030
Chapter 8. Vulnerability Scanning Tools Market – By End-User Industry
8.1 Introduction/Key Findings
8.2 Government and defence
8.3 IT and telecom
8.4 BFSI
8.5 Healthcare
8.6 Retail
8.7 Others
8.8 Y-O-Y Growth trend Analysis By End-User Industry
8.9 Absolute $ Opportunity Analysis By End-User Industry, 2024-2030
Chapter 9. Vulnerability Scanning Tools Market , By Geography – Market Size, Forecast, Trends & Insights
9.1 North America
9.1.1 By Country
9.1.1.1 U.S.A.
9.1.1.2 Canada
9.1.1.3 Mexico
9.1.2 By Deployment Model
9.1.3 By Organization Size
9.1.4 By End-User Industry
9.1.5 Countries & Segments - Market Attractiveness Analysis
9.2 Europe
9.2.1 By Country
9.2.1.1 U.K
9.2.1.2 Germany
9.2.1.3 France
9.2.1.4 Italy
9.2.1.5 Spain
9.2.1.6 Rest of Europe
9.2.2 By Deployment Model
9.2.3 By Organization Size
9.2.4 By End-User Industry
9.2.5 Countries & Segments - Market Attractiveness Analysis
9.3 Asia Pacific
9.3.1 By Country
9.3.1.1 China
9.3.1.2 Japan
9.3.1.3 South Korea
9.3.1.4 India
9.3.1.5 Australia & New Zealand
9.3.1.6 Rest of Asia-Pacific
9.3.2 By Deployment Model
9.3.3 By Organization Size
9.3.4 By End-User Industry
9.3.5 Countries & Segments - Market Attractiveness Analysis
9.4 South America
9.4.1 By Country
9.4.1.1 Brazil
9.4.1.2 Argentina
9.4.1.3 Colombia
9.4.1.4 Chile
9.4.1.5 Rest of South America
9.4.2 By Deployment Model
9.4.3 By Organization Size
9.4.4 By End-User Industry
9.4.5 Countries & Segments - Market Attractiveness Analysis
9.5 Middle East & Africa
9.5.1 By Country
9.5.1.1 United Arab Emirates (UAE)
9.5.1.2 Saudi Arabia
9.5.1.3 Qatar
9.5.1.4 Israel
9.5.1.5 South Africa
9.5.1.6 Nigeria
9.5.1.7 Kenya
9.5.1.8 Egypt
9.5.1.9 Rest of MEA
9.5.2 By Deployment Model
9.5.3 By Organization Size
9.5.4 By End-User Industry
9.5.5 Countries & Segments - Market Attractiveness Analysis
Chapter 10. Vulnerability Scanning Tools Market – Company Profiles – (Overview, Product Portfolio, Financials, Strategies & Developments)
10.1 Acunetix Ltd.
10.2 BeyondTrust Corporation
10.3 F-Secure Corporation
10.4 IBM Corporation
10.5 McAfee LLC
10.6 Nessus
10.7 Qualys, Inc.
10.8 Rapid7 LLC
10.9 Tenable, Inc.
10.10 Tripwire, Inc.
Download Sample
Choose License Type
2500
4250
5250
6900
Frequently Asked Questions
The Global Vulnerability Scanning Tools Market size will be valued at USD 11.73 billion in 2023.
The worldwide Global Vulnerability Scanning Tools Market growth is estimated to be 11.1% from 2024 to 2030.
The Global Vulnerability Scanning Tools Market is segmented By Deployment Model (On-Premises, Cloud-Based); By Organization Size (Small and Medium-Sized Enterprises (SMEs), Large Enterprises); By Type (Network Vulnerability Scanners, Web Application Vulnerability Scanners) and by region.
Tools for scanning for vulnerabilities have a bright future! A growing acceptance of cloud-based solutions for simpler deployment and scalability, as well as developments in AI and machine learning for even more intelligent threat detection, are to be anticipated. Vulnerability scanning will become an increasingly more important tool in an organization's cybersecurity armoury as rules and cyber threats continue to change.
The market for vulnerability scanning was impacted by the COVID-19 outbreak in a variety of ways. Although some people postponed expenditures due to financial difficulty, the demand for technologies to safeguard these larger attack surfaces was driven by the rise in remote work and increased cyberattacks. All things considered; it is anticipated that the long-term trend of growing cyberthreats will keep driving market expansion.



